China-linked APT Mustang Panda upgrades tools in its arsenal
China-linked APT group Mustang Panda deployed a new custom backdoor, MQsTTang, in recent attacks targeting Europe, Asia, and Australia. China-linked APT group Mustang Panda (aka Camaro Dragon, RedDelta or Bronze President). deployed a new custom backdoor, tracked as MQsTTang, in recent attacks targeting entities in Europe, Asia, and Australia. Mustang Panda has been active since […]
China-linked APT group Mustang Panda deployed a new custom backdoor, MQsTTang, in recent attacks targeting Europe, Asia, and Australia.
China-linked APT group Mustang Panda (aka Camaro Dragon, RedDelta or Bronze President). deployed a new custom backdoor, tracked as MQsTTang, in recent attacks targeting entities in Europe, Asia, and Australia.
Mustang Panda has been active since at least 2012, targeting American and European entities such as government organizations, think tanks, NGOs, and even Catholic organizations at the Vatican. Past campaigns were focused on Asian countries, including Taiwan, Hong Kong, Mongolia, Tibet, and Myanmar. In the 2022 campaigns, threat actors used European Union reports on the conflict in Ukraine and Ukrainian government reports as lures. Upon opening the reports, the infection process starts leading to the deployment of malware on the victim’s system.
In February 2024, Trend Micro researchers observed the group targeting Asian countries, including Taiwan, Vietnam, and Malaysia.
The Zscaler ThreatLabz team recently identified new activity linked to the Mustang Panda, originating from two machines within a targeted organization in Myanmar. This investigation uncovered new variants of the ToneShell backdoor and several previously undocumented tools, including StarProxy, Paklog and Corklog keyloggers, and the SplatCloak EDR evasion driver.
The APT employs DLL sideloading by packaging malicious libraries with vulnerable executables, enabling stealthy execution of payloads and evasion of detection.
The experts analyzed three distinct variants of the ToneShell backdoor, each utilizing DLL sideloading to execute malicious payloads. All the variants are distributed within archives containing a legitimate executable and a malicious DLL:
- Variant 1: Archive
cf.rarincludesmrender.exeandlibcef.dll. - Variant 2: Archive
ru.zipincludesFastVD.exeandLogMeIn.dll. - Variant 3: Archive
zz.rarincludesgpgconf.exeandlibgcrypt-20.dll.
Key Features across the three variants are:
- GUID Generation: Each variant generates a unique identifier (GUID) for the infected machine, employing different methods to derive seeds for random number generation.
- Rolling XOR Key: Utilized for encrypting communications with the command-and-control (C2) server, with key sizes varying among variants.
- FakeTLS Headers: Employed to mimic legitimate TLS traffic, aiding in evasion of network-based detections.
- C2 Commands: Variants support a range of commands, including file operations, reverse shell creation, and DLL injection, allowing for flexible control over compromised systems.
These adaptations reflect Mustang Panda’s ongoing efforts to refine the tools in their arsenal for enhanced stealth and functionality.
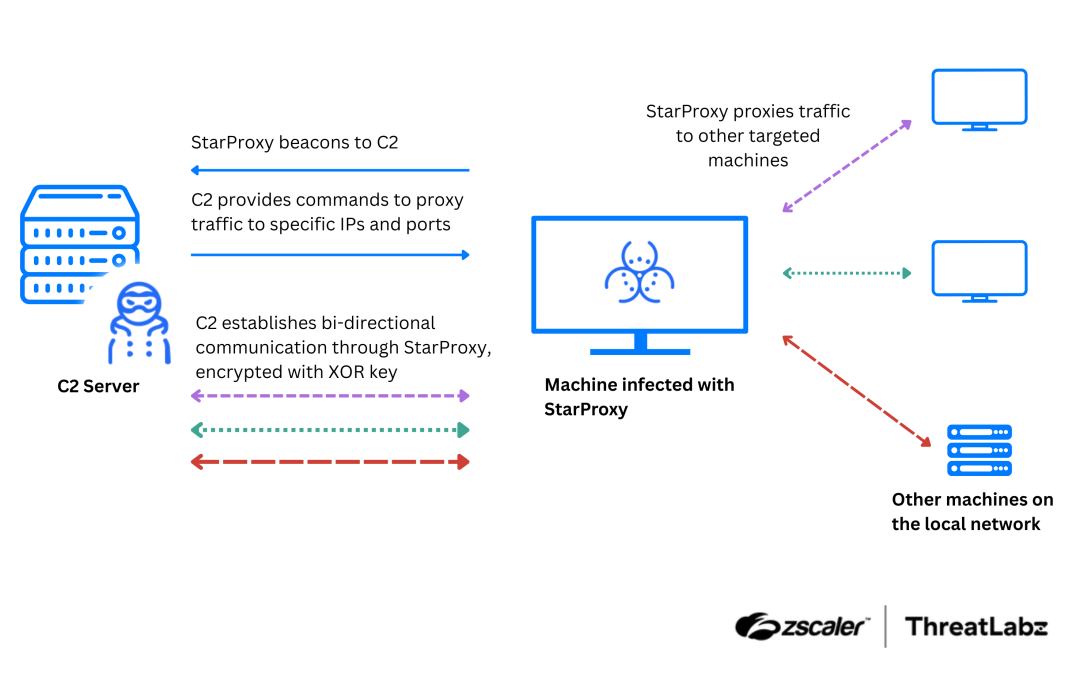
ThreatLabz researchers have identified a new tool, named StarProxy, used by Mustang Panda for lateral movement. Discovered within a RAR archive containing a legitimate executable (IsoBurner.exe) and a malicious DLL (StarBurn.dll), StarProxy employs DLL sideloading to activate upon execution. Once active, it proxies traffic between infected devices and command-and-control servers using TCP sockets and FakeTLS, encrypting data with a custom XOR-based algorithm. Command-line arguments specify IP addresses and ports, facilitating data relay through compromised machines. This design suggests its use as a post-compromise tool to access systems not directly reachable over the Internet.

“ToneShell, a backdoor used by Mustang Panda, has been updated with changes to its FakeTLS command-and-control (C2) communication protocol as well as to the methods for creating and storing client identifiers.” concludes the report. “Mustang Panda remains active in targeting organizations and individuals in Myanmar.”
The report includes Indicators of Compromise (IOCs) for this threat. Zscaler also published a Part 2 analysis, which provides additional details about the two new keyloggers and an EDR evasion driver employed by the APT group.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Mustang Panda)