Godfather Android trojan uses virtualization to hijack banking and crypto apps
Godfather Android trojan uses virtualization to hijack banking and crypto apps, stealing user funds, warns mobile security firm Zimperium. Zimperium zLabs has uncovered a major evolution of the GodFather Android trojan, which uses on-device virtualization to hijack real banking and crypto apps. Instead of using fake overlays, the malware creates a sandbox on the victim’s […]
Godfather Android trojan uses virtualization to hijack banking and crypto apps, stealing user funds, warns mobile security firm Zimperium.
Zimperium zLabs has uncovered a major evolution of the GodFather Android trojan, which uses on-device virtualization to hijack real banking and crypto apps. Instead of using fake overlays, the malware creates a sandbox on the victim’s device, runs actual apps inside it, and intercepts user input in real time. This technique allows for full account takeovers and bypasses security features. The current campaign targets Turkish banks and shows a serious leap in mobile malware tactics.
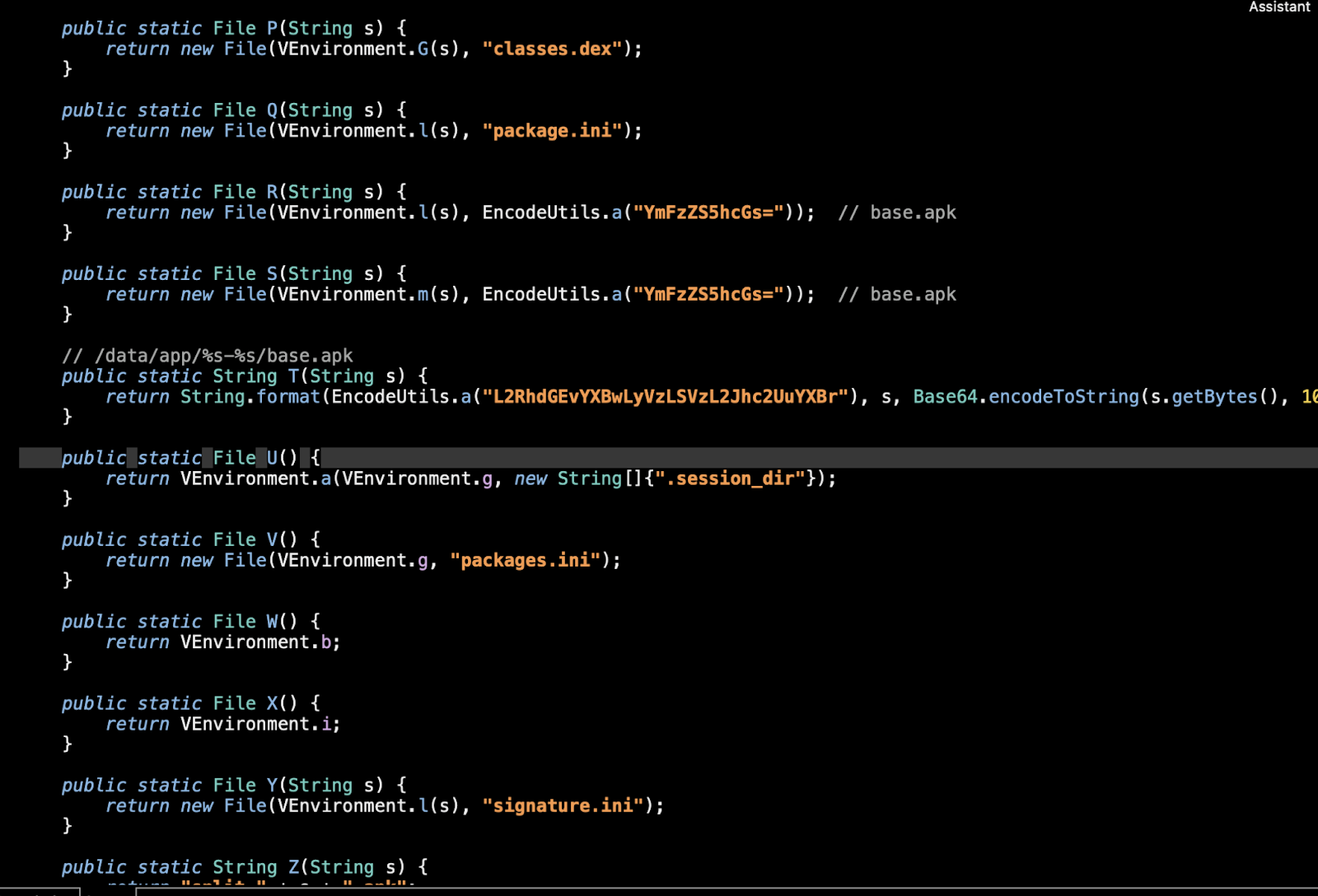
The latest GodFather Android malware samples use ZIP manipulation and obfuscation to evade static analysis. Threat actors tamper with APK ZIP structure and the Android Manifest, adding flags and fields like “$JADXBLOCK” to mislead tools. The malware hides its payload in the assets folder and uses session-based installation to bypass restrictions. It exploits accessibility services to monitor user input, auto-grant permissions, and exfiltrate data to a C2 server via Base64-encoded URLs.
The GodFather malware uses legit open-source tools like Virtualapp and Xposed to run overlay attacks. It virtualizes apps inside a host container, not on the Android OS directly.

Hosted apps run in a sandboxed file system managed by the host, with the process com.heb.reb:va_core executing them. This setup lets the malware hook APIs, steal data, and stay hidden, ensuring its malicious functions run undetected in a controlled environment.
The GodFather malware uses a clever virtualization trick to hijack banking apps on Android devices. First, it scans the victim’s phone for specific banking apps. If it finds any, it downloads and installs Google Play components into a hidden virtual space it controls.
Next, it sets up a fake environment where it can secretly run those real banking apps. It copies key data from the legitimate apps, like package names and security details, into special files (like package.ini). This allows the malware to launch real banking apps inside its sandbox, keeping user sessions intact.
When a user tries to open their actual banking app, GodFather intercepts the request and redirects them to a fake version inside its virtual space. It uses Android’s accessibility services and its own proxy tools to seamlessly mimic the look and behavior of the real app. The victim thinks they’re using their trusted bank app, but in reality, every tap and login is being captured.
In short, GodFather creates a virtual clone of your banking app to steal your info without you noticing.
“This virtualization technique provides attackers with several critical advantages over previously seen malware. By running the legitimate app inside a controlled environment, attackers gain total visibility into the application’s processes, allowing them to intercept credentials and sensitive data in real-time. The malware can be controlled remotely and also use hooking frameworks to modify the behavior of the virtualized app, effectively bypassing security checks such as root detection. In addition to this core technique, GodFather has evolved its evasive maneuvers, employing ZIP manipulation and shifting code to the Java layer to defeat static analysis tools.” reads the report published by Zimperium. “Crucially, because the user is interacting with the real, unaltered application, the attack achieves perfect deception, making it nearly impossible to detect through visual inspection and neutralizing user vigilance.”
The GodFather malware implements advanced hooking techniques to spy on banking apps. It tailors its attack to each app, using the Xposed framework to intercept network connections, especially through the OkHttpClient library, which many banking apps use. It injects malicious interceptors to log sensitive data like login credentials.
The malware also hides itself from detection by hooking Android’s getEnabledAccessibilityServiceList API, making it return an empty list so it appears invisible to security checks.
Worse still, GodFather can steal lock screen credentials. It does this by showing fake overlays that mimic real lock screens, tricking users into entering their PIN, password, or pattern. Once entered, the malware captures that info, putting the entire device at risk.
The malware supports a wide range of commands that allow attackers to simulate gestures, manipulate screen elements, open apps/settings, control brightness, and even steal lock screen credentials through fake overlays.
It uses both advanced virtualization and classic overlay techniques to hijack legitimate apps, especially targeting over 484 popular applications. These include:
- Banking & financial apps across the U.S., Europe, and Turkey
- Cryptocurrency wallets and exchanges
- E-commerce, ride-sharing, food delivery, and streaming apps
- Social media and messaging platforms
The malware’s modular command system lets it perform precise, stealthy actions like launching fake apps, executing gestures, faking updates, controlling screen content, and stealing sensitive data, all while staying hidden from users and security tools.
“While this GodFather campaign casts a wide net, targeting nearly 500 applications globally, our analysis reveals that this highly sophisticated virtualization attack is currently focused on a dozen Turkish financial institutions.” concludes the report. “This discovery represents a significant leap in capability beyond previously documented research like “FjordPhantom” and the most recent publicly available analysis reported by Cyble in November 2024.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)