Google Threat Intelligence Group (GTIG) tracked 75 actively exploited zero-day flaws in 2024
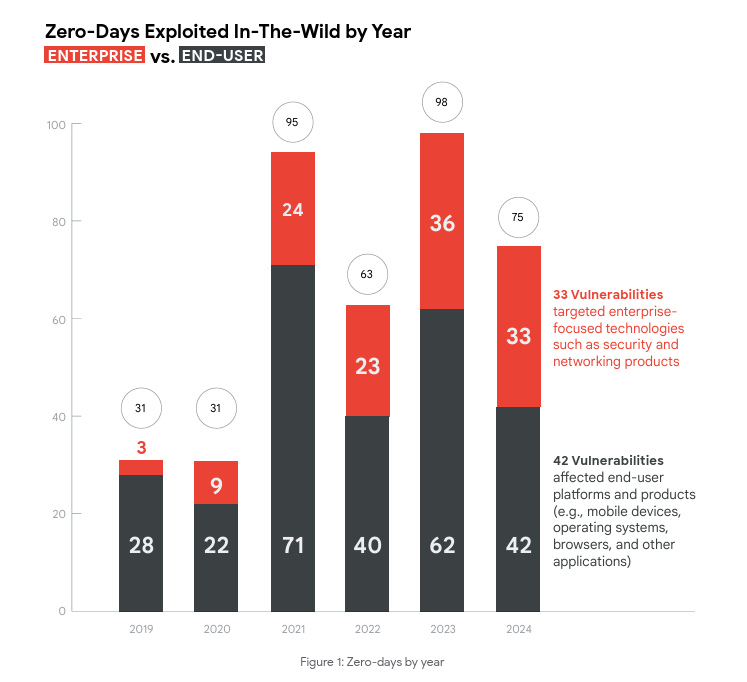
Google tracked 75 zero-day flaws exploited in 2024, down from 98 in 2023, according to its Threat Intelligence Group’s latest analysis. In 2024, Google tracked 75 exploited zero-day vulnerabilities, down from 98 in 2023 but up from 63 in 2022. The researchers from Google Threat Intelligence Group (GTIG) observed that most targeted are end-user platforms, […]
Google tracked 75 zero-day flaws exploited in 2024, down from 98 in 2023, according to its Threat Intelligence Group’s latest analysis.
In 2024, Google tracked 75 exploited zero-day vulnerabilities, down from 98 in 2023 but up from 63 in 2022. The researchers from Google Threat Intelligence Group (GTIG) observed that most targeted are end-user platforms, though attacks on enterprise tech are rising. The report published by GTIG highlights evolving attacker tactics, better vendor defenses, and growing challenges in detecting commercial surveillance activity.
“GTIG continued to observe an increase in adversary exploitation of enterprise-specific technologies throughout 2024. In 2023, 37% of zero-day vulnerabilities targeted enterprise products.” reads the report published GTIG. “This jumped to 44% in 2024, primarily fueled by the increased exploitation of security and networking software and appliances.”
In 2024, over 60% of zero-day exploits targeting enterprise tech hit security and networking tools, offering attackers efficient access to systems and networks.
GTIG experts reported that in 2024, zero-day attacks targeting enterprise tech grew, while browser and mobile exploits dropped. End-user platforms saw 56% of zero-day activity. Chrome remained the most targeted web browser, while mobile attacks often used exploit chains. Desktop OS zero-days rose to 22, with Microsoft Windows continuing to be a major target due to its widespread use.
“Microsoft Windows exploitation continued to increase, climbing from 13 zero-days in 2022, to 16 in 2023, to 22 in 2024.” continues the report. “As long as Windows remains a popular choice both in homes and professional settings, we expect that it will remain a popular target for both zero-day and n-day (i.e. a vulnerability exploited after its patch has been released) exploitation by threat actors.”
Enterprise products like Ivanti, Palo Alto, and Cisco are prime targets due to limited EDR monitoring and the ability of single flaws to enable full system compromise.
In 2024, over half of zero-days enabled remote code execution or privilege escalation. Use-after-free, command injection, and XSS were the top vulnerabilities. According to the report, most attacks targeted security and network software. Google attributed 34 cases, with 53% tied to cyber espionage groups, mainly nation-state or commercial surveillance vendors.

“While we still expect government-backed actors to continue their historic role as major players in zeroday exploitation, CSVs now contribute a significant volume of zero-day exploitation. Although the total count and proportion of zero-days attributed to CSVs declined from 2023 to 2024, likely in part due to their increased emphasis on operational security practices, the 2024 count is still substantially higher than the count from 2022 and years prior.” concludes the report. “Their role further demonstrates the expansion of the landscape and the increased access to zero-day exploitation that these vendors now provide other actors.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, zero-days)