Ivanti fixed two EPMM flaws exploited in limited attacks
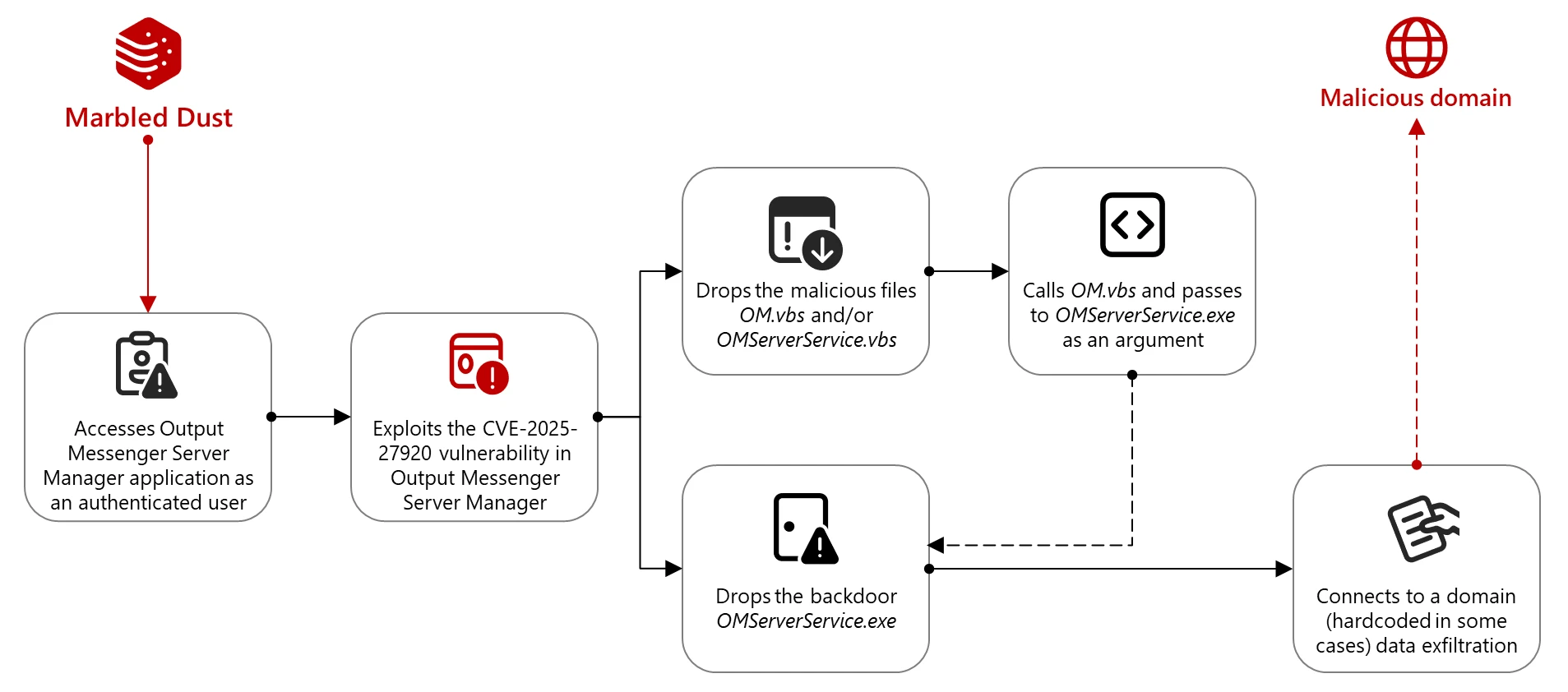
Ivanti addressed two Endpoint Manager Mobile (EPMM) software vulnerabilities that have been exploited in limited attacks. Ivanti has released security updates to address two vulnerabilities in Endpoint Manager Mobile (EPMM) software. The company confirmed that threat actors have chained the flaws in limited attacks to gain remote code execution. The two vulnerabilities are tracked as CVE-2025-4427 and […]

Ivanti addressed two Endpoint Manager Mobile (EPMM) software vulnerabilities that have been exploited in limited attacks.
Ivanti has released security updates to address two vulnerabilities in Endpoint Manager Mobile (EPMM) software. The company confirmed that threat actors have chained the flaws in limited attacks to gain remote code execution.
The two vulnerabilities are tracked as CVE-2025-4427 and CVE-2025-4428, below are their description:
- CVE-2025-4427 (CVSS score: 5.3) – An authentication bypass in Endpoint Manager Mobile allowing attackers to access protected resources without proper credentials.
- CVE-2025-4428 (CVSS score: 7.2) – A remote code execution vulnerability in Endpoint Manager Mobile allowing attackers to execute arbitrary code on the target system.
CERT-EU reported both vulnerabilities to the software firm.
The company confirmed that threat actors could chain the two vulnerabilities to achieve remote code execution without authentication.
“Ivantii has released updates for Endpoint Manager Mobile (EPMM) which addresses one medium and one high severity vulnerability. When chained together, successful exploitation could lead to unauthenticated remote code execution.” reads the advisory. “We are aware of a very limited number of customers whose solution has been exploited at the time of disclosure.”
Below is the list of the impacted software versions:
Product Name Affected Version(s) Affected CPE(s) Resolved Version(s) Patch Availability Endpoint Manager Mobile 11.12.0.4 and prior 12.3.0.1 and prior 12.4.0.1 and prior 12.5.0.0 and prior cpe:2.3:a:ivanti:endpoint_manager_mobile:11.12.0.0:*:*:*:*:*:*:* cpe:2.3:a:ivanti:endpoint_manager_mobile:11.12.0.1:*:*:*:*:*:*:* cpe:2.3:a:ivanti:endpoint_manager_mobile:11.12.0.2:*:*:*:*:*:*:* cpe:2.3:a:ivanti:endpoint_manager_mobile:11.12.0.3:*:*:*:*:*:*:* cpe:2.3:a:ivanti:endpoint_manager_mobile:12.3.0.0:*:*:*:*:*:*:* 11.12.0.5 12.3.0.2 12.4.0.2 12.5.0.1 Download Portal: https://forums.ivanti.com/s/product-downloads
The vulnerabilities have been addressed with versions 11.12.0.5, 12.3.0.2, 12.4.0.2, or 12.5.0.1.
The vulnerabilities affect two unnamed open-source libraries used in EPMM, the company pointed out that they don’t reside in their code.
The company is still investigating the attacks, however, it does not have “reliable atomic indicators” at the time of this writing.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, EPMM)