Malicious Go Modules designed to wipe Linux systems
Researchers found 3 malicious Go modules with hidden code that can download payloads to wipe a Linux system’s main disk, making it unbootable. The malicious modules contain obfuscated code to fetch next-stage payloads that can wipe a Linux system’s primary disk and make it unbootable. “Socket’s Threat Research Team uncovered a stealthy and highly destructive […]
Researchers found 3 malicious Go modules with hidden code that can download payloads to wipe a Linux system’s main disk, making it unbootable.
The malicious modules contain obfuscated code to fetch next-stage payloads that can wipe a Linux system’s primary disk and make it unbootable.
“Socket’s Threat Research Team uncovered a stealthy and highly destructive supply-chain attack targeting developers using Go modules.” read the report published by Socket. “Attackers leveraged obfuscation to deliver a catastrophic disk-wiper payload.”
Below are the names of the malware-laced modules:
- github[.]com/truthfulpharm/prototransform
- github[.]com/blankloggia/go-mcp
- github[.]com/steelpoor/tlsproxy
The researchers warn that unlike centralized package managers such as npm or PyPI, the Go ecosystem’s decentralized nature where modules are directly imported from GitHub repositories creates substantial confusion. Developers often encounter multiple similarly named modules with entirely different maintainers. This ambiguity makes it exceptionally challenging to identify legitimate packages from malicious ones, even when packages aren’t strictly “typosquatted.” Attackers exploit this confusion, carefully crafting their malicious module namespaces to appear trustworthy at a glance, increasing the likelihood that developers inadvertently integrate malicious code into their projects.

The three malicious Go modules check the OS before execution, ensuring that the malicious code is executed online on Linux environments.
Malicious Go modules fetched and executed a destructive shell script from attacker-controlled servers, leaving no time to react. Similar tactics were seen in past attacks.
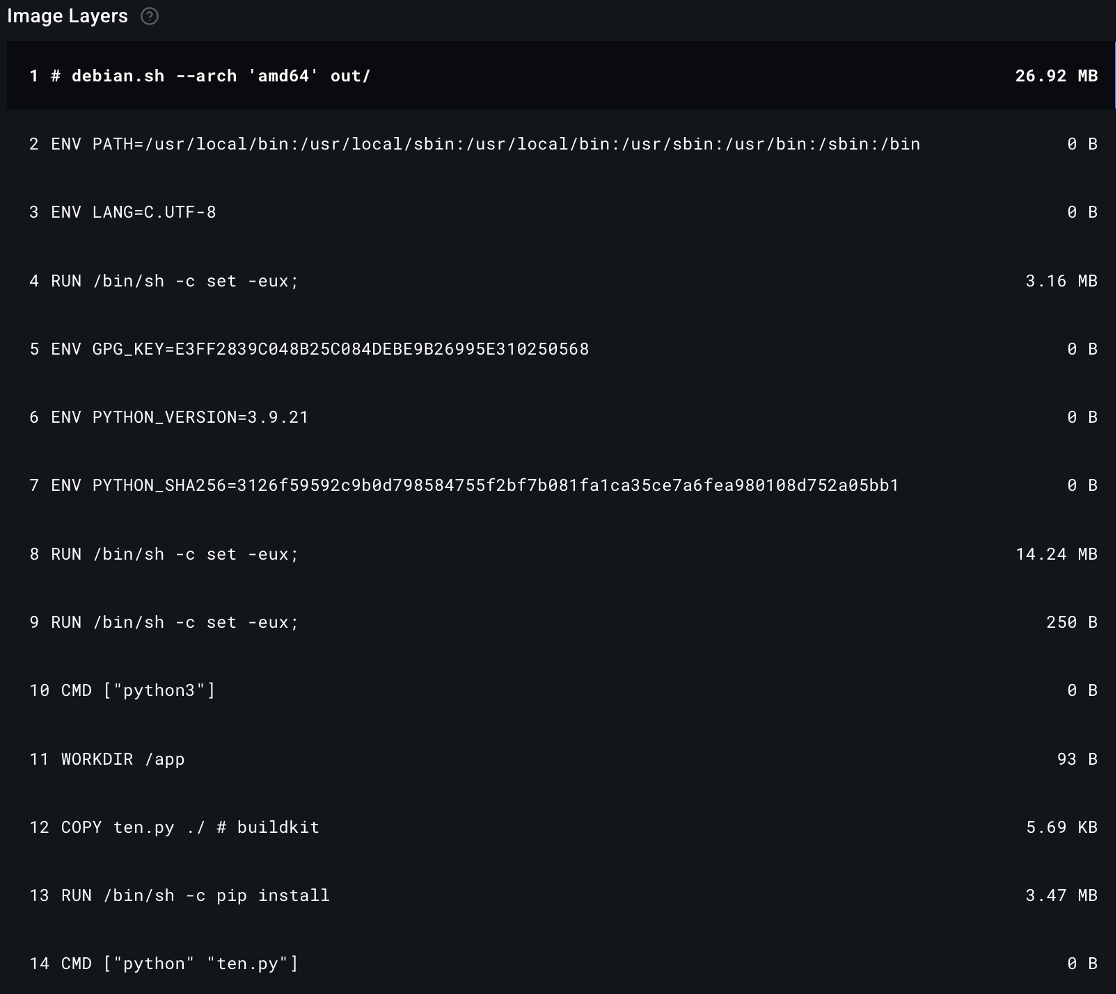
One of the downloaded payloads observed by the experts contained a destructive wiper shell script, done.sh, which overwrites the entire primary Linux disk (/dev/sda) with zeros, permanently destroying all data and rendering the system unbootable.
“This destructive method ensures no data recovery tool or forensic process can restore the data, as it directly and irreversibly overwrites it.” continues the report. “This malicious script leaves targeted Linux servers or developer environments entirely crippled, highlighting the extreme danger posed by modern supply-chain attacks that can turn seemingly trusted code into devastating threats.”
The executions of the malicious modules can cause total data loss, major downtime, and severe financial and reputational harm, highlighting the need for strong supply chain security.
“Secure software development practices must evolve to address these sophisticated threats. Proactive code audits, automated dependency analysis, and continuous runtime monitoring must become integral to the software development lifecycle, particularly for projects heavily reliant on external open source dependencies.” concludes the expert.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, newsletter)