Police took down several popular counter-antivirus (CAV) services, including AvCheck
On May 27, 2025, authorities seized crypting service sites (including AvCheck, Cryptor, and Crypt.guru) used by vxers to test malware evasion capabilities. An international law enforcement operation led by the U.S. Department of Justice has dismantled an online cybercrime syndicate that provided encryption services to help malware evade detection. On May 27, 2025, authorities seized […]
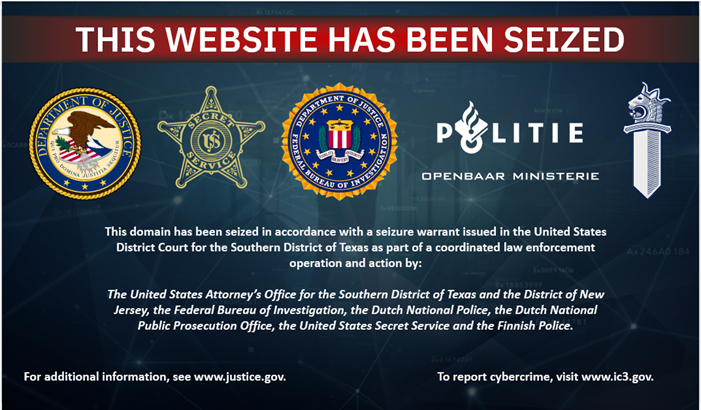
On May 27, 2025, authorities seized crypting service sites (including AvCheck, Cryptor, and Crypt.guru) used by vxers to test malware evasion capabilities.
An international law enforcement operation led by the U.S. Department of Justice has dismantled an online cybercrime syndicate that provided encryption services to help malware evade detection. On May 27, 2025, authorities seized four domains, including AvCheck[.]net, Cryptor[.]biz, and Crypt[.]guru.
The seizures took place on May 27 as part of Operation Endgame, a global effort led by U.S., Dutch, Finnish, and other national police to shut down malware services. Countries like France, Germany, and Denmark joined the operation, with support from Ukraine and Portugal.
“Crypting is the process of using software to make malware difficult for antivirus programs to detect,” the DoJ said. “The seized domains offered services to cybercriminals, including counter-antivirus (CAV) tools.” reads the press release published by DoJ. “When used together, CAV and crypting services allow criminals to obfuscate malware, making it undetectable and enabling unauthorized access to computer systems.”
CAV services, like AVCheck, let cybercriminals test their malware against antivirus programs to see if it will go undetected. This helps them launch stealthy attacks and gain access to victims’ systems without being noticed, making these services a key tool in the cybercrime ecosystem.
DoJ revealed that undercover agents bought and tested the services provided by the seized websites, confirming they were built for cybercrime. Evidence, including email links, tied the services to known ransomware groups behind attacks in the U.S. and abroad, some even targeting the Houston area.
“Cybercriminals don’t just create malware; they perfect it for maximum destruction,” said FBI Houston Special Agent in Charge Douglas Williams. “By leveraging counter antivirus services, malicious actors refine their weapons against the world’s toughest security systems to better slip past firewalls, evade forensic analysis, and wreak havoc across victims’ systems. As part of a decisive international operation, FBI Houston helped cripple a global cyber syndicate, seize their most lethal tools, and neutralize the threat they posed to millions around the world.”
Dutch police, in coordination with U.S. and Finnish authorities, also published an announcement to reveal it has dismantled AVCheck, a major service used by malware developers.
“The service that has been taken down is AVCheck, one of the largest Counter Antivirus (CAV) services used by cybercriminals around the world.” reads the Dutch police’s announcement. “‘Taking AVCheck offline is an important step in the fight against organised cybercrime,’ says Matthijs Jaspers, Team Lead of the High Tech Crime Team, ‘because it disrupts the activities of cybercriminals in the earliest stages and prevents victims.’”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, AvCheck)