The LockBit ransomware site was breached, database dump was leaked online
Lockbit ransomware group has been compromised, attackers stole and leaked data contained in the backend infrastructure of their dark web site. Hackers compromised the dark web leak site of the LockBit ransomware gang and defaced it, posting a message and a link to the dump of the MySQL database of its backend affiliate panel. “Don’t […]
Lockbit ransomware group has been compromised, attackers stole and leaked data contained in the backend infrastructure of their dark web site.
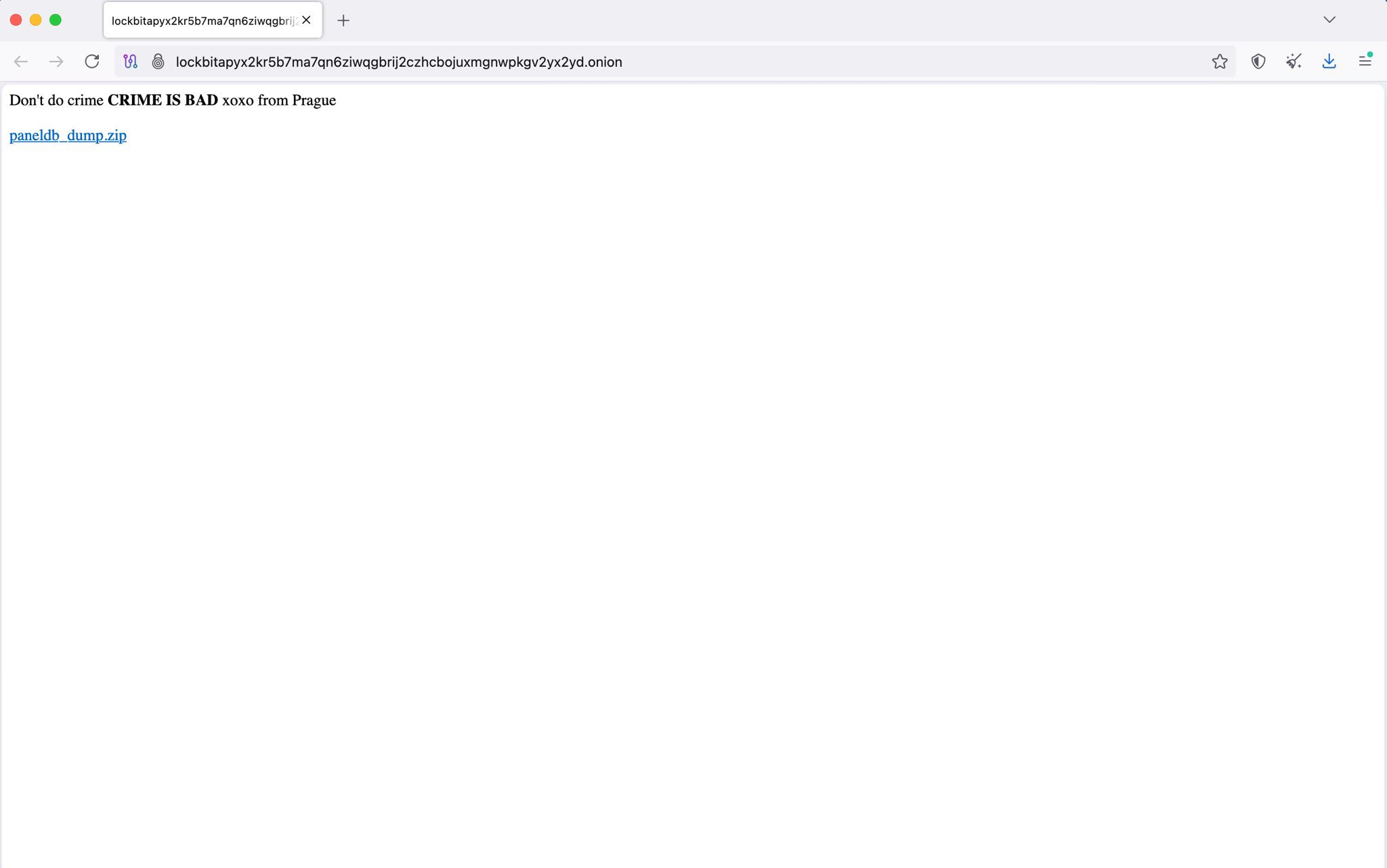
Hackers compromised the dark web leak site of the LockBit ransomware gang and defaced it, posting a message and a link to the dump of the MySQL database of its backend affiliate panel.
“Don’t do crime CRIME IS BAD xoxo from Prague,” reads the message published on the group dark web leak site.

The LockBit operator ‘LockBitSupp’ confirmed the data breach in a private conversation with the threat actor Rey, however, he said that no private keys were leaked or data lost.
“A ‘chats‘ table is very interesting as it contains 4,442 negotiation messages between the ransomware operation and victims from December 19th to April 29th.” states BleepingComputer.
Researchers noticed that only 44 user accounts are associated with actual encryptor builds for LockBit affiliates, among which 30 were active at the moment of the dump.