China-linked UnsolicitedBooker APT used new backdoor MarsSnake in recent attacks
China-linked UnsolicitedBooker used a new backdoor, MarsSnake, to target an international organization in Saudi Arabia. ESET researchers revealed that a China-linked APT, tracked as UnsolicitedBooker, targeted an international organization in Saudi Arabia using a new backdoor called MarsSnake. The experts uncovered the attacks in March 2023 and again in 2024, noting that the group used […]
China-linked UnsolicitedBooker used a new backdoor, MarsSnake, to target an international organization in Saudi Arabia.
ESET researchers revealed that a China-linked APT, tracked as UnsolicitedBooker, targeted an international organization in Saudi Arabia using a new backdoor called MarsSnake. The experts uncovered the attacks in March 2023 and again in 2024, noting that the group used spear-phishing emails with fake flight ticket lures to breach systems.
UnsolicitedBooker has repeatedly targeted government organizations in Asia, Africa, and the Middle East, using spear-phishing emails to deliver malware. Their toolkit includes backdoors such as Chinoxy, DeedRAT, Poison Ivy, and BeRAT, commonly associated with Chinese APT groups.
The above backdoors are shared among multiple China-linked APT groups.
“The group also deployed custom file stealers; therefore, we believe that the motivation of this threat actor is espionage and data theft. UnsolicitedBooker sends spearphishing emails, generally with a flight ticket as the decoy, and its targets include governmental organizations in Asia, Africa, and the Middle East.” reads the report published by ESET. “According to our investigation, UnsolicitedBooker overlaps with both Space Pirates and an unnamed threat actor that uses the Zardoor backdoor.”
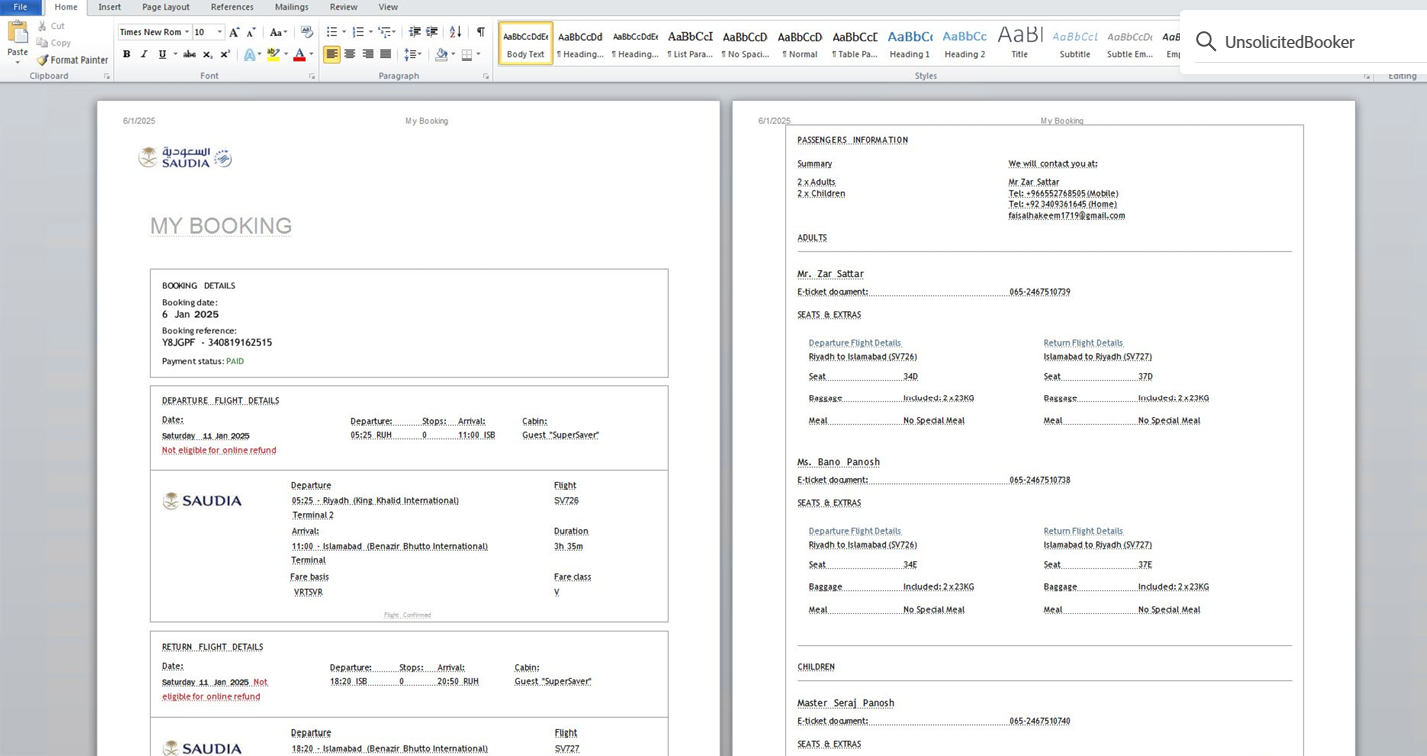
In January 2025, UnsolicitedBooker launched another spearphishing attack against the same Saudi organization previously targeted. The phishing email, impersonating Saudia airline, came from saudia.etickets@outlook[.]com and included a fake flight ticket in a Word document, based on a PDF from Academia.edu.
The researchers observed that in 2024, UnsolicitedBooker reused the same ticket decoy from earlier attacks, embedding a VBA macro that drops a MarsSnake backdoor loader. The payload is saved as smssdrvhost.exe, and PDB paths confirm the MarsSnake name. The threat actors used the C&C server contact.decenttoy[.]top. Two more phishing attempts were also detected at the same target.
“The multiple attempts at compromising this organization in 2023, 2024, and 2025 indicate a strong interest by UnsolicitedBooker in this specific target.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)