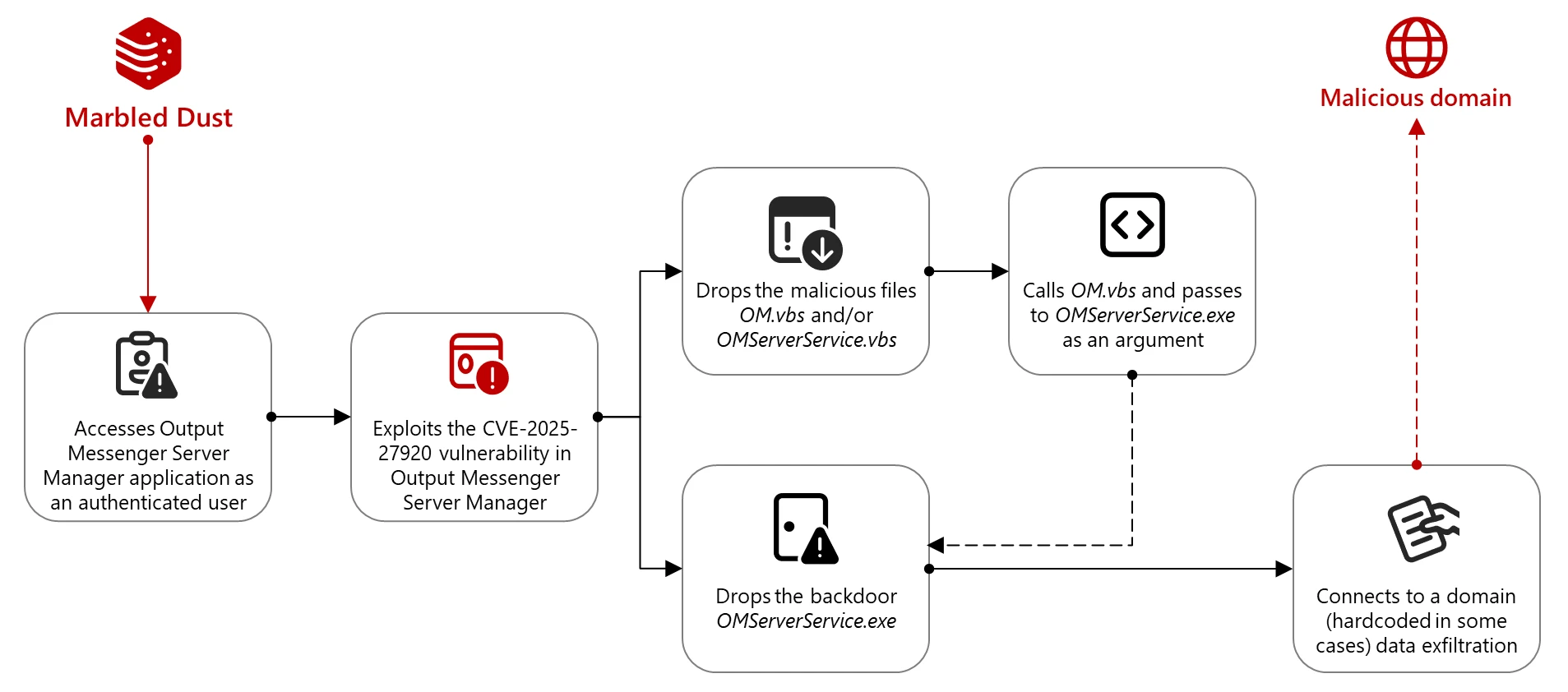
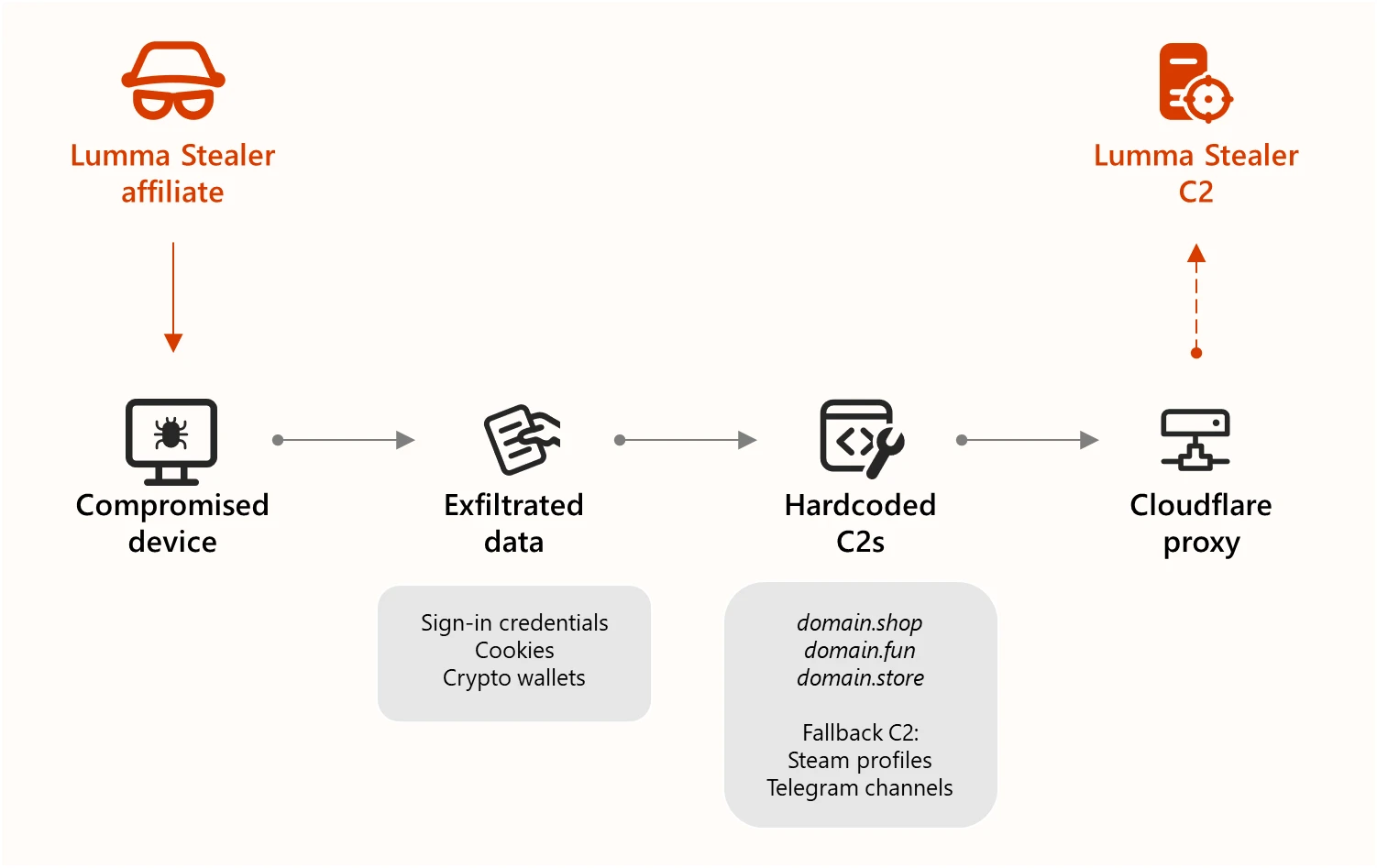
Operation ENDGAME disrupted global ransomware infrastructure
Operation ENDGAME dismantled key ransomware infrastructure, taking down 300 servers, 650 domains, and seizing €21.2M in crypto. From May 19 to 22, 2025, Operation ENDGAME, coordinated by Europol and Eurojust, disrupted global ransomware infrastructure. Law enforcement took down down 300 servers and 650 domains, and issuing 20 international arrest warrants. “A Command Post was set […]

Operation ENDGAME dismantled key ransomware infrastructure, taking down 300 servers, 650 domains, and seizing €21.2M in crypto.
From May 19 to 22, 2025, Operation ENDGAME, coordinated by Europol and Eurojust, disrupted global ransomware infrastructure. Law enforcement took down down 300 servers and 650 domains, and issuing 20 international arrest warrants.
“A Command Post was set up at Europol headquarters in The Hague during the action week, with investigators from Canada, Denmark, France, Germany, the Netherlands, the United Kingdom and the United States working with Europol’s European Cybercrime Centre and its Joint Cybercrime Action Taskforce.” reads the press release published by Europol. “Eurojust has provided essential support to make judicial cooperation effective since the beginning of the investigation in 2024. Coordination by Eurojust ensured that authorities were able to exchange information and align their investigative efforts.”
Authorities also seized €3.5M in cryptocurrency, bringing the total to over €21.2M. This follows the 2024 botnet crackdown, targeting evolving malware threats and cybercriminal groups.
The operation targeted initial access malware used by threat actors to infiltrate systems prior to ransomware deployment. Neutralized strains include Bumblebee, Lactrodectus, Qakbot, Hijackloader, DanaBot, Trickbot, and Warmcookie, all commonly used in ransomware-as-a-service schemes. Authorities also issued 20 international arrest warrants for key operators.
Several key suspects behind malware operations are now under international and public alerts. Germany will list 18 of them on the EU Most Wanted list from May 23. They allegedly provided or operated tools used in major ransomware attacks.
“This new phase demonstrates law enforcement’s ability to adapt and strike again, even as cybercriminals retool and reorganise. By disrupting the services criminals rely on to deploy ransomware, we are breaking the kill chain at its source.” said Catherine De Bolle, Europol Executive Director.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Operation ENDGAME)